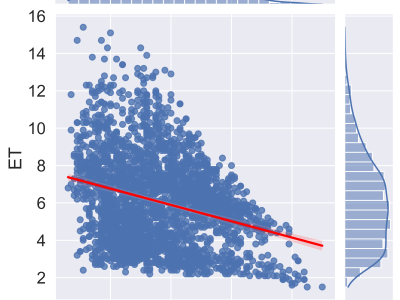
Reference Evapotranspiration (ETo) is the basic element of smart irrigation water management for sustainable developments in agriculture. Penman-Monteith (FAO-56 PM) is the standard method of ETo. The FAO-56 PM is complex in nature due to the requirements of many climatic conditions. Many existing machine learning-based solutions for simplification of ETo are limited to a specific area and not in accordance with the standard method FAO-56 PM.
- Categories:



