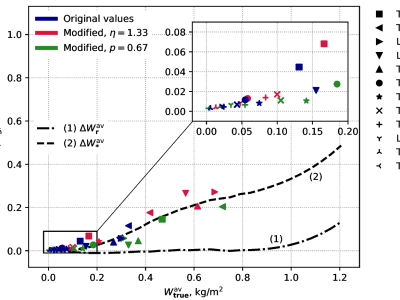
The recent developments in the field of the Internet of Things (IoT) bring alongside them quite a few advantages. Examples include real-time condition monitoring, remote control and operation and sometimes even remote fault remediation. Still, despite bringing invaluable benefits, IoT-enriched entities inherently suffer from security and privacy issues. This is partially due to the utilization of insecure communication protocols such as the Open Charge Point Protocol (OCPP) 1.6. OCPP 1.6 is an application-layer communication protocol used for managing electric vehicle chargers.
- Categories: