Machine Learning
Guava fruit production is one of the main sources of economic growth in Asian countries, the world production of guava in 2019 was 55 million tons. Guava disease is an important factor in economic loss as well as quantity and quality of guava. The original guava fruit disease dataset consist of 38 images of phytophthora, 30 images of root and 34 images of scab guava disease with 650x650x3 pixel.
- Categories:
 1279 Views
1279 ViewsA synthetic laser reliability dataset generated using generative adversarial networks (GANs) is provided. The data includes normalized current measurements estimated at the following times: 2, 20, 40, 60, 80, 100, 150, 500, 1000, and 1500 hours. The data can be used to train machine learning models to solve different predictive maintenance tasks such as prediction of performance degradation, remainng useful prediction, and so on.
- Categories:
 140 Views
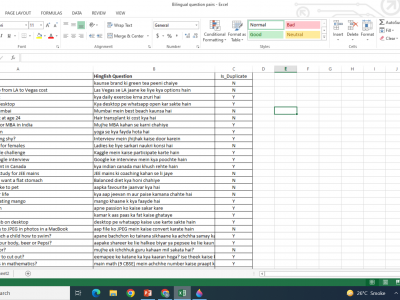
140 ViewsAlthough asking and replying on social media platforms in mixed language is a very common phenomenon these days, there is lack of precise corpora to analyze such code mixed language. Datasets released by various CQA sites are monolingual i.e. only in English language. To perform our task, we needed annotated bilingual dataset which include Question pairs in mashed up language. In view of this scarcity we created a dataset by scraping pairs of questions from distinct social media networks, for-example Yahoo!
- Categories:
 126 Views
126 Views
The dataset contains labeled sentences. The sentences having information related to (1) infections, (2) suffering from pneumonea, (3) deaths, and (4) health updates from government/WHO, are labeled with 1 and the rest are labeled with 0. Source of all the news articles: https://www.thehindu.com/archive/
- Categories:
 130 Views
130 ViewsPROTEIN STRUCTURE AND SYNTHETIC MULTI-VIEW CLUSTERING DATASETS
Multi-View Clustering (MVC) datasets used in the following paper:
Evolutionary Multi-objective Clustering Over Multiple Conflicting Data Views. Authors: Mario Garza-Fabre, Julia Handl, and Adán José-García. IEEE TRANSACTIONS ON EVOLUTIONARY COMPUTATION. Accepted for publication, November 2022.
This entry contains all 420 datasets used in the paper, including:
- Categories:
 268 Views
268 ViewsThis synthetic dataset is generated using Matlab automotive driving toolbox to simulate a 77GHz FMCW millimeter-wave radar sensing in the road scenario. Especially for the Doppler ambiguity case, when the object vehicles move within or out of the unambiguous detecable velocity range. The dataset contains in total 20 recordings with the duration of 1 second each. Both time-division modulation (TDM) and binary phase modulation (BPM) data are provided. Each recording consists of complex ADC raw data and complex range-Doppler map, together with the ground-truth range and velocity.
- Categories:
 472 Views
472 Views
Biometric management and that to which uses face, is indeed a very challenging work and requires a dedicated dataset which imbibes in it variations in pose, emotion and even occlusions. The Current work aims at delivering a dataset for training and testing purposes.SJB Face dataset is one such Indian face image dataset, which can be used to recognize faces. SJB Face dataset contains face images which were collected from digital camera. The face dataset collected has certain conditions such as different pose, Expressions, face partially occluded and with a uniform attire.
- Categories:
 2936 Views
2936 ViewsEvolving from the well-known ray-tracing dataset DeepMIMO, the DeepVerse 6G dataset additionally provides multi-modal sensing data generated from various emulators. These emulators provide the wireless, radar, LiDAR, vision and position data. With a parametric generator, the DeepVerse dataset can be customized by the user for various communication and sensing applications.
- Categories:
 189 Views
189 ViewsBeam management is a challenging task for millimeter wave (mmWave) and sub-terahertz communication systems, especially in scenarios with highly-mobile users. Leveraging external sensing modalities such as vision, LiDAR, radar, position, or a combination of them, to address this beam management challenge has recently attracted increasing interest from both academia and industry. This is mainly motivated by the dependency of the beam direction decision on the user location and the geometry of the surrounding environment---information that can be acquired from the sensory data.
- Categories:
 1076 Views
1076 Views