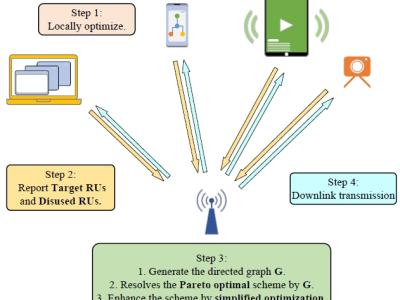
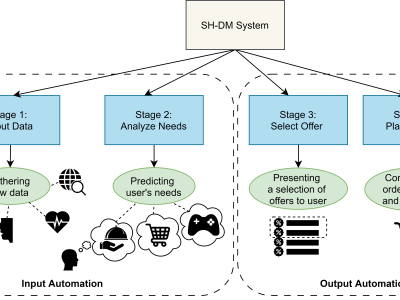
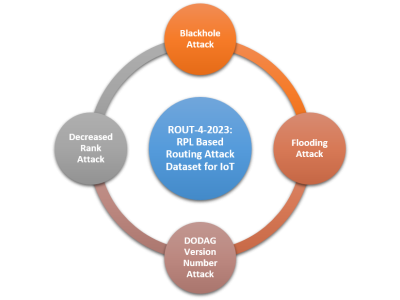
This dataset presents a comprehensive collection of research articles on requirements engineering, encompassing various subtopics such as requirements specification, elicitation techniques, software development methodologies, and challenges in requirements management. The dataset includes metadata such as publication year, author details, research titles, objectives, problem statements, identified gaps, key findings, and contributions.
- Categories: