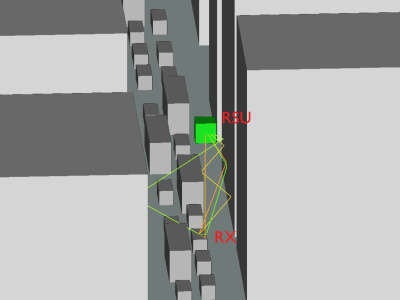
Data and codes for journal paper "MmWave Vehicular Beam Training with Situational Awareness Using Machine Learning" submitted to IEEE Access.
The code assumes Python 3.
- Categories:

Data and codes for journal paper "MmWave Vehicular Beam Training with Situational Awareness Using Machine Learning" submitted to IEEE Access.
The code assumes Python 3.
이 그룹은 음향 장비 분야의 음향 증폭기 회로에 실리콘 트랜지스터를 사용할 때 오디오 관점에서 출력 신호의 음향 특성을 향상시키는 것을 목표로합니다.
음향 증폭기 회로에서 실리콘 트랜지스터를 사용할 때 사운드 출력은 차갑고 거칠고 선명하며 풍부하지 않은 것으로 알려져 있습니다. 따라서 오디오 애호가들은 여전히 진공관을 사용하는 증폭기를 좋아합니다. 오디오 애호가는 소리를들을 수있는 능력 때문에 음질을 판단하는 뛰어난 능력을 가지고 있습니다.
그래서이 그룹은 실리콘 트랜지스터의 불충분 한 사운드 특성을 제거하고 튜브의 사운드로 개선하는 방법을 보여줍니다.
이 개선 방법을 적용하여이 부분을 만드는 과정을 논의하고 마지막으로 실제 부분으로 만들 것입니다.
한국어로 쓰여진 원본이 포함되어 있습니다.
여러 파일 중 가장 큰 개정 번호 만 사용하십시오.
나머지는 비교를위한 데이터입니다.
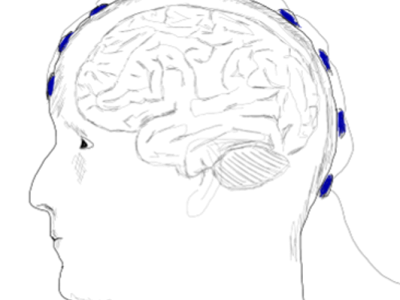
This material is associated with the PhD Thesis of Javier Olias (which is supervised by Sergio Cruces) and the article:
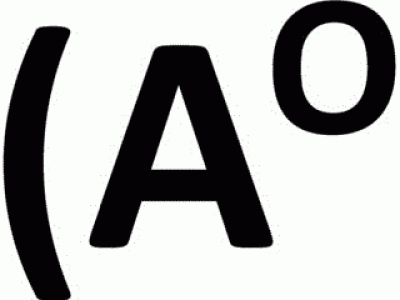
The presented dataset has been used as a basis for CAO - a system for analysis of emoticons in Japanese online communication, developed by Ptaszynski et al. (2010). Emoticons are strings of symbols widely used in text-based online communication to convey user emotions. The database contains: 1) a predetermined raw emoticon database containing over ten thousand emoticon samples extracted from the Web, 2) emoticon parts automatically divided from raw emoticons into semantic areas representing “mouths” or “eyes”.

HTTP and DNS sample traffic traces for experimenting of protocol reverse engineering methods.
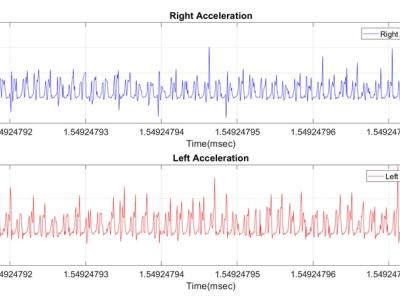
AoT for Smart Society provides solutions of industry 4.0 standards in which contains custom-built multisensory wearable suit with cloud connectivity interfaced Artificial Intelligent techniques and Machine Learning algorithms in order to detect, to monitor and to analyze biofeedback control and visualization during human daily activities.

Date fruit data sets are not publicly available. Previous studies have collected and used their own data set. Almost all these studies have few hundred images per class. As our motive was robust date fruit classification, we did not use the camera to take images of a particular size, angle or images with a particular background, instead to add robustness, we built our date fruit database using Google search engine. Hence the images had the multi-background, noise, different lighting condition, other objects, different packaging and sometimes even partial covering.

Lists of file hashes used in SDAC: A Slow-Aging Solution for Android Malware Detection Using Semantic Distance Based API Clustering

This is the LVSiM simulator files

We have included the code of protocol verification for ProVerif (in .pv format) and Scyther (in .spdl format) in the “Supplementary Materials” (Supplementary-Materials.pdf) of the revised manuscript. Essentially, the .pdf file of the “Supplementary Materials” includes: A. The source code for the protocol verifier Scyther (in .spdl format); and B. The source code for the protocol verifier ProVerif (in .pv format).