*.pcap (zip)
Due to the large number of vulnerabilities in information systems and the continuous activity of attackers, techniques for malicious traffic detection are required to identify and protect against cyber-attacks. Therefore, it is important to intentionally operate a cyber environment to be invaded and compromised in order to allow security professionals to analyze the evolution of the various attacks and exploited vulnerabilities.
This dataset includes 2016, 2017 and 2018 cyber attacks in the HoneySELK environment.
- Categories:
 5211 Views
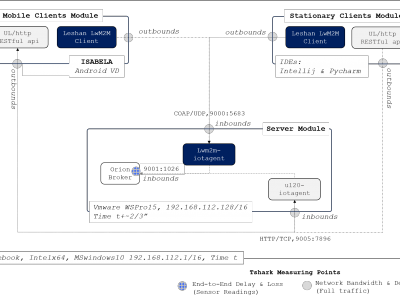
5211 ViewsMessage Queuing Telemetry Transport (MQTT) protocol is one of the most used standards used in Internet of Things (IoT) machine to machine communication. The increase in the number of available IoT devices and used protocols reinforce the need for new and robust Intrusion Detection Systems (IDS). However, building IoT IDS requires the availability of datasets to process, train and evaluate these models. The dataset presented in this paper is the first to simulate an MQTT-based network. The dataset is generated using a simulated MQTT network architecture.
- Categories:
 25045 Views
25045 Views
The dataset contains a set of voip flows (with different codecs) captured in fixed/fixed and fixed/mobile LTE-A enviroment.
- Categories:
 1152 Views
1152 Views