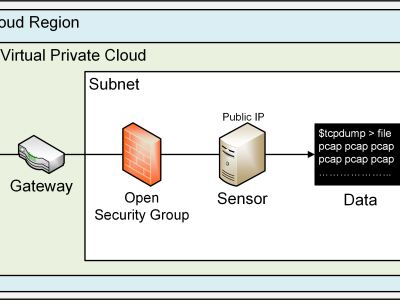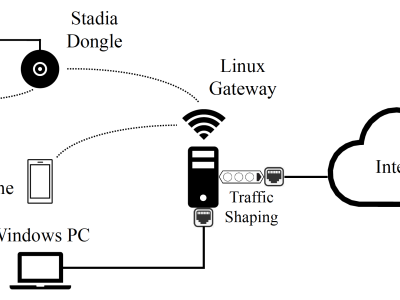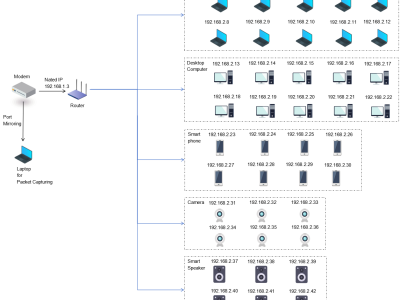
three-level network topology experimental environment was constructed based on a typical home network. An optical network terminal (Bell XE-140W-TD) was used as the starting point for Internet access, and a Gigabit wired connection was established with the core router (Huawei TC30) via a shielded Cat 6 cable. This router is a Huawei beta version that can obtain specific device information and corresponding traffic after NAT. The experimental evaluation of traffic attribution association in subsequent chapters will use this as ground truth label data for comparison.
- Categories: