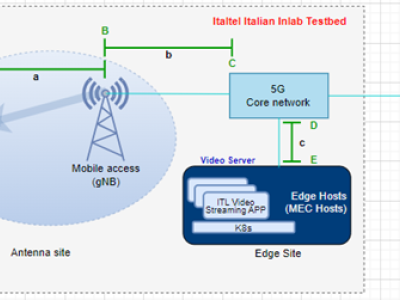
This dataset comprises residential energy data from the UK, covering a nearly five-year period from 2015 to 2020. It includes a total of 201,605 data points, each meticulously recorded at 15-minute intervals, ensuring a high level of granularity. The dataset provides detailed attributes such as the date, time, residential energy load (measured in kilowatts), electricity price (in GBP), solar energy generation (in kilowatts), wind energy generation (in kilowatts), and various weather-related parameters.
- Categories: