IoT

Spreadsheet use for conversion of visible light lux measurements to irradiance.
Back up for manuscript: Calculation of Visible Light Irradiance from Lux Illuminance and Relative Spectral Illuminance
- Categories:
 341 Views
341 ViewsThis is a CSI dataset towards 5G NR high-precision positioning,
which is fine-grained, general-purpose and 3GPP R18 standards complied.
The corresponding paper is published here (https://doi.org/10.1109/jsac.2022.3157397).
5G NR is normally considered to as a new paradigm change in integrated sensing and communication (ISAC).
- Categories:
 6888 Views
6888 Views
The uploaded data are for the paper: "A Wearable Skin Temperature Monitoring System for Early Detection of Infections". Baseline kin temperature measurement data from all 5 volunteers (subjects) who wore the wearable band for 3-5 days are included along with 5-day temperature measurement data with anomalies of one volunteer who wore both the smart band and a heating pad. Augmented data generated using the methods described in the paper for COVID-19 infection anomaly detection are also included
- Categories:
 638 Views
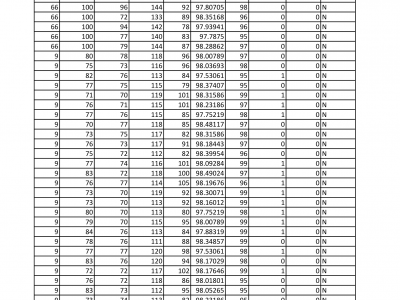
638 ViewsThe given Dataset is record of different age group people either diabetic or non diabetic for theie blood glucose level reading with superficial body features like body temperature, heart rate, blood pressure etc.
The main purpose of the dataset is to understand the effect of blood glucose level on human body.
The different superficial body parameters show sifnificant variation according to change in blood glucose level.
- Categories:
 10911 Views
10911 ViewsContext
This dataset consists of subject wise daily living activity data, which is acquired from the inbuilt accelerometer and gyroscope sensors of the smartphones.
Content
The smartphone was mounted on the waist and front pockets of the users. All the different activities were performed in a laboratory except Running, which was performed on a Football Playground.
Smartphone used: Poco X2 and Samsung Galaxy A32s
Inbuild Sensors used: Accelerometer and Gyroscope
Ages: All subjects are Above 23 years
- Categories:
 2991 Views
2991 Views
Packet delivery ratio data collected for the article Wireless-Sensor Network Topology Optimization in Complex Terrain: A Bayesian Approach. Published in the IEEE Internet of Things Journal.
- Categories:
 147 Views
147 Views
The cell characterization scripts and ultra low voltage flip-flop design information including 320-bit (16x20) parallel shift register design....
If you use this data, please add the citation to the following paper :
- Categories:
 132 Views
132 Views