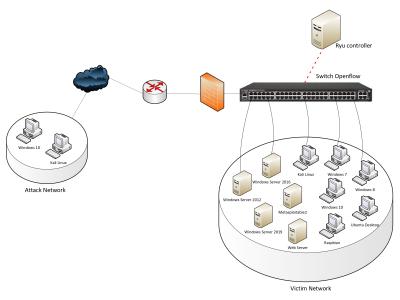
This unlabeled dataset reflects the network activity of a real branch office with 29 active machines connected to the same broadcast domain for four hours. To achieve this, a Network Intrusion Detection System (NIDS) called BCAST IDS listened to network traffic every 10 seconds. During this time, various types of activities were carried out (browsing, emailing, file transfers, etc.) on each machine to ensure the dataset reflected a wide range of benign behavior.
- Categories: