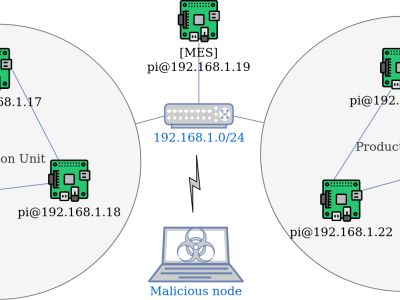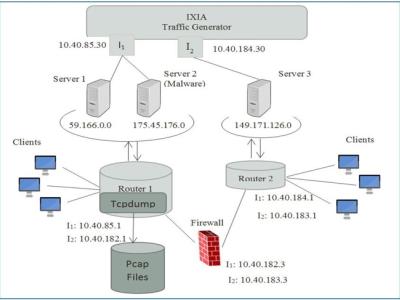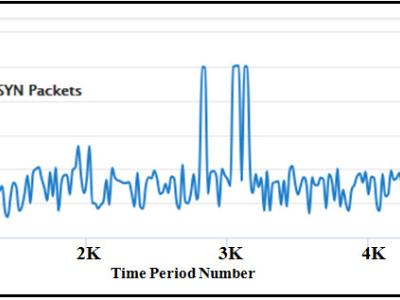
Distributed Denial of Service (DDoS) attacks first appeared in the mid-1990s, as attacks stopping legitimate users from accessing specific services available on the Internet. A DDoS attack attempts to exhaust the resources of the victim to crash or suspend its services. Time series modeling will help system administrators for better planning of resource allocation to defend against DDoS attacks. Different Time Series analysis techniques are applied to detect the DDoS attacks.
- Categories: