Artificial Intelligence

Our DeepCoAST dataset specifically explores the vulnerabilities of various traffic-splitting Website Fingerprinting (WF) Defenses, such as TrafficSliver, HyWF, and CoMPS. Our dataset comprises defended traces generated from the BigEnough dataset, which includes Tor cell trace instances of 95 websites, each represented by 200 instances collected under the standard browser security level. We simulated the traffic-splitting defenses assuming there are two split traces from the vanilla trace.
- Categories:
 46 Views
46 Views
The safe implementation and adoption of Autonomous Vehicle (AV) vision models on public roads requires not only an understanding of the natural environment comprising pedestrians and other vehicles but also the ability to reason about edge situations such as unpredictable maneuvers by other drivers, impending accidents, erratic movement of pedestrians, cyclists, and motorcyclists, animal crossings, and cyclists using hand signals.
- Categories:
 84 Views
84 ViewsThis dataset contains both the artificial and real flower images of bramble flowers. The real images were taken with a realsense D435 camera inside the West Virginia University greenhouse. All the flowers are annotated in YOLO format with bounding box and class name. The trained weights after training also have been provided. They can be used with the python script provided to detect the bramble flowers. Also the classifier can classify whether the flowers center is visible or hidden which will be helpful in precision pollination projects.
- Categories:
 385 Views
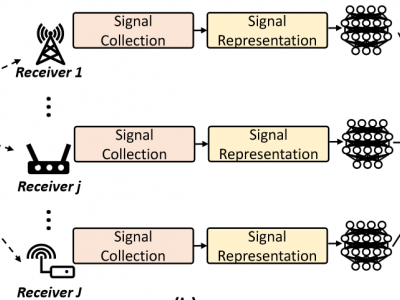
385 ViewsRadio frequency fingerprint identification (RFFI) is an emerging device authentication technique, which exploits the hardware characteristics of the RF front-end as device identifiers. The receiver hardware impairments interfere with the feature extraction of transmitter impairments, but their effect and mitigation have not been comprehensively studied. In this paper, we propose a receiver-agnostic RFFI system by employing adversarial training to learn the receiver-independent features.
- Categories:
 401 Views
401 Views
This is the relevant data in "Monocular Homography Estimation and Positioning Method for the Spatial-Temporal Distribution of Vehicle Loads Identification".
- Categories:
 125 Views
125 Views
The public UA-DETRAC data set was used to train the vehicle target detection model in this study. This data set was captured predominantly in the Beijing-Tianjin-Hebei area. Using a Canon EOS 550 camera, 10 hours of video were captured at 25 frames per second, and then the footage was processed. Each frame had a resolution of 960*540 pixels. The UA-DETRAC data set contained 8,259 manually labeled vehicles, with a total of 1,210,000 labeled vehicles. The labeled types included cars, buses, trucks, etc.
- Categories:
 643 Views
643 Views
The dataset crafted for this study is intentionally designed to encapsulate instances of cyberbullying across three distinct languages: Urdu, Roman Urdu, and English. This strategic selection aims to mirror the linguistic variations that are prevalent in social media dialogues among Urdu-speaking communities globally. Further, it undergoes meticulous annotation to encapsulate the diverse linguistic nuances characteristic of these languages. This process includes integrating critical aspects of cyberbullying, such as aggression, repetition, and intent to harm.
- Categories:
 372 Views
372 Views
Coming soon. Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat. Duis aute irure dolor in reprehenderit in voluptate velit esse cillum dolore eu fugiat nulla pariatur. Excepteur sint occaecat cupidatat non proident, sunt in culpa qui officia deserunt mollit anim id est la
- Categories:
 303 Views
303 Views
This work selects two real datasets, namely Diginetica and Yoochoose. Diginetica is employed in CIKM Cup 2016, which contains user's transaction data. Yoochoose is released in Recsys Challenge 2015 as a public dataset and mainly consists of click data within six months. For better recommendation, we follow previous work and preprocess the real datasets.
- Categories:
 107 Views
107 Views