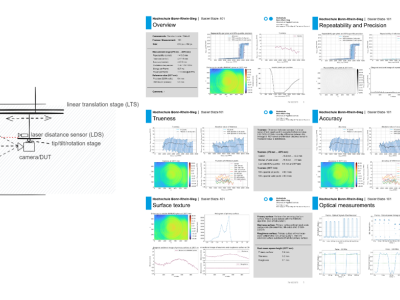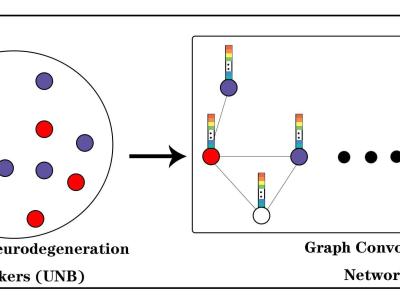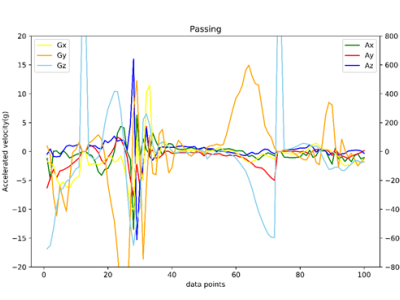
The dataset contains basketball activity data for nine varsity basketball players of professional skill levels. Each player wore a smart bracelet on their right wrist to record activity data during the event. The smart bracelet contains an accelerometer and gyroscope that collects acceleration and angular velocity information, and it has a sampling frequency of 50 Hz. The basketball activities of the players are laying up, passing and shooting, which are defined as shown in Table 1.
- Categories: