Other

This data is associated with the manuscript "A Systematic Operational Performance Evaluation Framework for Public-Private Partnership Transportation Infrastructure Projects" . It is derived from the questionnaire used in the study.
- Categories:
 19 Views
19 ViewsThis code is with the submitted manuscript "Decentralized Optimal Coverage Control of Constant-Speed Unicycle Multi-Agent Systems Subject to State- and Input-Dependent Constraints". The code consists of MATLAB scripts and should be run in MATLAB. No version limitation and no additional toolboxes are required.
- Categories:
 199 Views
199 Views
This dataset contains RAW data of BaTiO3, CaTiO3 and SrTiO3 buffer layer on LaAlO3 substrate and YBCO grown MTO-buffered substrates. Several techniques such as TGA, SEM and XRD were introduced.
- Categories:
 104 Views
104 Views
This is the dataset containing the original data for article "Investigating Thermionic Emission Properties of Polycrystalline Perovskite BaMoO3" submitted to IEEE TED.
- Categories:
 89 Views
89 Views
Dataset for the paper titled "Comparing Three Generations of D-Wave Quantum Annealers for Minor Embedded Combinatorial Optimization Problems". This data includes the minor embeddings and raw D-Wave measurements.
- Categories:
 105 Views
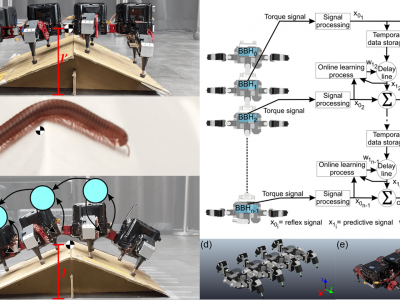
105 ViewsTypically, control strategies for legged robots have been developed to adapt their leg movements to deal with complex terrain. When the legs are extended in search of ground contact to support the robot body, this can result in the center of gravity (CoG) being raised higher from the ground and can lead to unstable locomotion if it deviates from the support polygon. An alternative approach is body adaptation, inspired by millipede/centipede locomotion behavior, which can result in low ground clearance and stable locomotion.
- Categories:
 212 Views
212 ViewsA reliable and extensive set of public WiFi fingerprinting radio map databases for researchers to implement, evaluate and compare Wi-Fi RSSI indoor localization schemes, the radio map database contains RSSI information from more than 400 APs collected during the conducted experiment on different days with the support of lab mates and volunteers.
- Categories:
 1331 Views
1331 Views
For Internet-based service companies, anomaly detection on data streams is critical in troubleshooting, seeking to maintain service quality and reliability. Most of known detection methods have an underlying assumption that the data are always continuous. In practical applications, however, we learn that many real-world data are sporadic. It incurs particular challenges for the task of anomaly detection, for which the common preprocessing of downsampling on sporadic data can omit potential anomalies and delay alarms.
- Categories:
 42 Views
42 Views