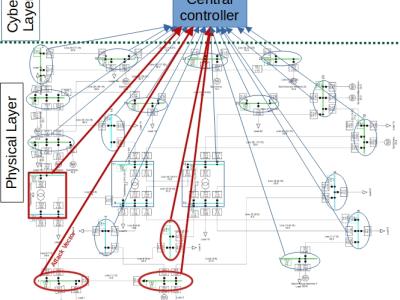
The performance, repeatability, and stability of the sensor were measured,Sensors are applied to gesture recognition and human-computer interaction. By utilizing wavelength division multiplexing technology, multiple sensors measure finger movements and improve recognition accuracy through backpropagation neural network algorithms. Five commonly used gestures were recognized and the sensor posture was determined based on light intensity.
- Categories: