DNP3 Intrusion Detection Dataset

- Citation Author(s):
- Submitted by:
- Panagiotis Sarigiannidis
- Last updated:
- DOI:
- 10.21227/s7h0-b081
- Data Format:
- Research Article Link:
 5499 views
5499 views
- Categories:
- Keywords:
Abstract
In the digital era of the Industrial Internet of Things (IIoT), the conventional Critical Infrastructures (CIs) are transformed into smart environments with multiple benefits, such as pervasive control, self-monitoring and self-healing. However, this evolution is characterised by several cyberthreats due to the necessary presence of insecure technologies. DNP3 is an industrial communication protocol which is widely adopted in the CIs of the US. In particular, DNP3 allows the remote communication between Industrial Control Systems (ICS) and Supervisory Control and Data Acquisition (SCADA). It can support various topologies, such as Master-Slave, Multi-Drop, Hierarchical and Multiple-Server. Initially, the architectural model of DNP3 consists of three layers: (a) Application Layer, (b) Transport Layer and (c) Data Link Layer. However, DNP3 can be now incorporated into the Transmission Control Protocol/Internet Protocol (TCP/IP) stack as an application-layer protocol. However, similarly to other industrial protocols (e.g., Modbus and IEC 60870-5-104), DNP3 is characterised by severe security issues since it does not include any authentication or authorisation mechanisms. This dataset contains labelled Transmission Control Protocol (TCP) / Internet Protocol (IP) network flow statistics (Common-Separated Values - CSV format) and DNP3 flow statistics (CSV format) related to 9 DNP3 cyberattacks. These cyberattacks are focused on DNP3 unauthorised commands and Denial of Service (DoS). The network traffic data are provided through Packet Capture (PCAP) files. Consequently, this dataset can be used to implement Artificial Intelligence (AI)-powered Intrusion Detection and Prevention (IDPS) systems that rely on Machine Learning (ML) and Deep Learning (DL) techniques
Instructions:
This DNP3 Intrusion Detection Dataset was implemented following the methodological frameworks of A. Gharib et al. in [4] and S. Dadkhah et al in [5], including eleven features: (a) Complete Network Configuration, (b) Complete Traffic, (c) Labelled Dataset, (d) Complete Interaction, (e) Complete Capture, (f) Available Protocols, (g) Attack Diversity, (h) Heterogeneity, (i) Feature Set and (j) Metadata.
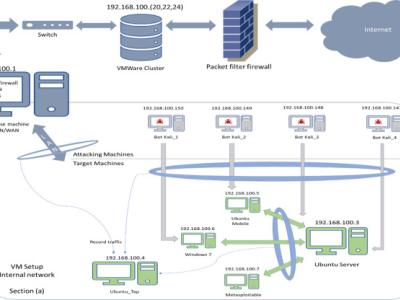
A network topology consisting of (a) eight industrial entities, (b) one Human Machine Interfaces (HMI) and (c) three cyberattackers was used to implement this DNP3 Intrusion Detection Dataset. In particular, the following cyberattacks were implemented.
•On Thursday, May 14, 2020, the DNP3 Disable Unsolicited Messages Attack was executed for 4 hours.
•On Friday, May 15, 2020, the DNP3 Cold Restart Message Attack was executed for 4 hours.
•On Friday, May 15, 2020, the DNP3 Warm Restart Message Attack was executed for 4 hours.
•On Saturday, May 16, 2020, the DNP3 Enumerate Attack was executed for 4 hours.
•On Saturday, May 16, 2020, the DNP3 Info Attack was executed for 4 hours.
•On Monday, May 18, 2020, the DNP3 Initialisation Attack was executed for 4 hours.
•On Monday, May 18, 2020, the Man In The Middle (MITM)-DoS Attack was executed for 4 hours.
•On Monday, May 18, 2020, the DNP3 Replay Attack was executed for 4 hours.
•On Tuesday, May 19, 2020, the DNP3 Stop Application Attack was executed for 4 hours.
The aforementioned DNP3 cyberattacks were executed, utilising penetration testing tools, such as Nmap and Scapy . For each attack, a relevant folder is provided, including the network traffic and the network flow statistics for each entity. In particular, for each cyberattack, a folder is given, providing (a) the pcap files for each entity, (b) the Transmission Control Protocol (TCP)/ Internet Protocol (IP) network flow statistics for 120 seconds in a CSV format and (c) the DNP3 flow statistics for each entity (using different timeout values in terms of second (such as 45, 60, 75, 90, 120 and 240 seconds)). The TCP/IP network flow statistics were produced by using the CICFlowMeter , while the DNP3 flow statistics were generated based on a Custom DNP3 Python Parser , taking full advantage of Scapy.
The dataset consists of the following folders:
•20200514_DNP3_Disable_Unsolicited_Messages_Attack: It includes the pcap and CSV files related to the DNP3 Disable Unsolicited Message attack.
•20200515_DNP3_Cold_Restart_Attack: It includes the pcap and CSV files related to the DNP3 Cold Restart attack.
•20200515_DNP3_Warm_Restart_Attack: It includes the pcap and CSV files related to DNP3 Warm Restart attack.
•20200516_DNP3_Enumerate: It includes the pcap and CSV files related to the DNP3 Enumerate attack.
•20200516_DNP3_Ιnfo: It includes the pcap and CSV files related to the DNP3 Info attack.
•20200518_DNP3_Initialize_Data_Attack: It includes the pcap and CSV files related to the DNP3 Data Initialisation attack.
•20200518_DNP3_MITM_DoS: It includes the pcap and CSV files related to the DNP3 MITM-DoS attack.
•20200518_DNP3_Replay_Attack: It includes the pcap and CSV files related to the DNP3 replay attack.
•20200519_DNP3_Stop_Application_Attack: It includes the pcap and CSV files related to the DNP3 Stop Application attack.
•Training_Testing_Balanced_CSV_Files: It includes balanced CSV files from CICFlowMeter and the Custom DNP3 Python Parser that could be utilised for training ML and DL methods. Each folder includes different sub-folder for the corresponding flow timeout values used by the DNP3 Python Custom Parser. For CICFlowMeter, only the timeout value of 120 seconds was used.
Each folder includes respective subfolders related to the entities/devices (described in the following section) participating in each attack. In particular, for each entity/device, there is a folder including (a) the DNP3 network traffic (pcap file) related to this entity/device during each attack, (b) the TCP/IP network flow statistics (CSV file) generated by CICFlowMeter for the timeout value of 120 seconds and finally (c) the DNP3 flow statistics (CSV file) from the Custom DNP3 Python Parser. Finally, it is noteworthy that the network flows from both CICFlowMeter and Custom DNP3 Python Parser in each CSV file are labelled based on the DNP3 cyberattacks executed for the generation of this dataset. The description of these attacks is provided in the following section, while the various features from CICFlowMeter and Custom DNP3 Python Parser are presented below.
The following figure shows the testbed utilised for the generation of this dataset. It is composed of eight industrial entities that play the role of the DNP3 outstations/slaves, such as Remote Terminal Units (RTUs) and Intelligent Electron Devices (IEDs). Moreover, there is another workstation which plays the role of the Master station like a Master Terminal Unit (MTU). For the communication between, the DNP3 outstations/slaves and the master station, opendnp3 was used.
The TCP/IP network flow statistics generated by CICFlowMeter are summarised below. The TCP/IP network flows and their statistics generated by CICFlowMeter are labelled based on the DNP3 attacks described above, thus allowing the training of ML/DL models. Finally, it is worth mentioning that these statistics are generated when the flow timeout value is equal with 120 seconds.
The DNP3 flow statistics generated by the DNP3 Python Parser are summarised below. The DNP3 flows and their statistics generated by the DNP3 Python Parser are labelled based on the DNP3 attacks described above, thus allowing the training of ML/DL models. Finally, it is worth mentioning that these statistics are available for various flow timeout values, such as 45, 60, 75, 90, 120 and 240 seconds.
The users of this dataset are kindly asked to cite the following papers as follows.
V. Kelli et al., "Attacking and Defending DNP3 ICS/SCADA Systems", 2022 18th International Conference on Distributed Computing in Sensor Systems (DCOSS), 2022, pp. 183-190, doi: 10.1109/DCOSS54816.2022.00041.
V. Kelli, P. Radoglou-Grammatikis, T. Lagkas, E. K. Markakis and P. Sarigiannidis, "Risk Analysis of DNP3 Attacks", 2022 IEEE International Conference on Cyber Security and Resilience (CSR), 2022, pp. 351-356, doi: 10.1109/CSR54599.2022.9850291.
P. Radoglou-Grammatikis, P. Sarigiannidis, G. Efstathopoulos, P.-A.Karypidis, and A. Sarigiannidis, "Diderot: An intrusion detection and prevention system for dnp3-based scada systems", in Proceedings of the15th International Conference on Availability, Reliability and Security, ser. ARES ’20.New York, NY, USA: Association for Computing Machinery, 2020, doi: 10.1145/3407023.3409314.
This project has received funding from the European Union’s Horizon 2020 research and innovation programme under grant agreements No 101021936 (ELECTRON) and No 833955 (SDN-microSENSE).









nice
Hi, could you please provie me the dataset, for my research on the development of my master thesis.
Could you please send it to me? "pg53820@uminho.pt".
Hi, could you provide me the dataset, for my research on Intelligence Mechanism for IOT Systems Sercurity?
My e-mail: duyanh314159@gmail.com