Open Access Entries from this Author
The "eternal war in cache" has reached browsers, with multiple cache-based side-channel attacks and countermeasures being suggested. A common approach for countermeasures is to disable or restrict JavaScript features deemed essential for carrying out attacks.
- Categories:
Category
TBD
- Categories:
Category

It is important for network operators to carry out traffic and application characterization to gain insights into the activity of their networks. Several studies proposed methods that extract features from network traffic to characterize it, or to classify the application that produced it, based on a ?man in the middle? network interception point that can analyze the entire network traffic of an organization.
- Categories:
Category
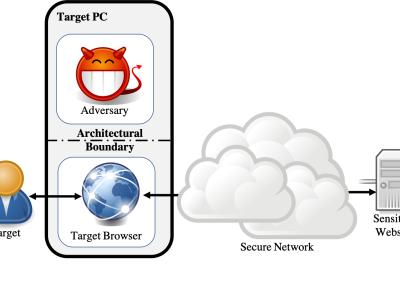
Website fingerprinting attacks, which use statistical analysis on network traffic to compromise user privacy, have been shown to be effective even if the traffic is sent over anonymity-preserving networks such as Tor. The classical attack model used to evaluate website fingerprinting attacks assumes an on-path adversary, who can observe all traffic traveling between the user's computer and the secure network.
- Categories:
Category
