IoT

Now days, everything in the world is almost becoming automated. Technology has changed the view through which earlier we used to look at the objects. In the 21st century, we are now opting for more easy options for accessing the technology and day to day objects. The best example is banking where in previous days; the account holder had to go far to the bank and stand in the queue and then transfer or cash the money. But same is now possible on even a basic cell phone where you can transfer the cash, pay the bills very easily not more than five minutes.
- Categories:
 148 Views
148 Views
Graphics provides one of the most natural means of communicating with a computer, since our highly developed 2D Or 3D pattern-recognition abilities allow us to perceive and process pictorial data rapidly. • Computers have become a powerful medium for the rapid and economical production of pictures. • Graphics provide a so natural means of communicating with the computer that they have become widespread. • Interactive graphics is the most important means of producing pictures since the invention of photography and television . • We can make pictures of not only the real world objects but als
- Categories:
 26 Views
26 Views
Tourism receipts worldwide are not expected to recover to 2019 levels until 2023. In
the first half of this year, tourist arrivals fell globally by more than 65 percent, with a near halt
since April—compared with 8 percent during the global financial crisis and 17 percent amid
the SARS epidemic of 2003, according to ongoing IMF research on tourism in a post-pandemic
world. Because of pandemic we faces the different struggles specially the business closed.
that’s why country’s economy decrease, at first many company need to reduce their employee.
- Categories:
 84 Views
84 Views
The data set includes attack implementations in an Internet of Things (IoT) context. The IoT nodes use Contiki-NG as their operating system and the data is collected from the Cooja simulation environment where a large number of network topologies are created. Blackhole and DIS-flooding attacks are implemented to attack the RPL routing protocol.
The datasets includes log file output from the Cooja simulator and a pre-processed feature set as input to an intrusion detection model.
- Categories:
 626 Views
626 ViewsThe Theory of Integrated Language Learning (ToILL) supports many complementary schools of educational thought. The constructivism, pragmatism, humanism, and sociocultural theory are combined in one process to produce an integrated and successful method of language acquisition. The approach promotes the complete person development in a continuously changing environment that is global in nature but does not stop at cognitive components but also concerns the social and emotional experiences of the students.
- Categories:
 259 Views
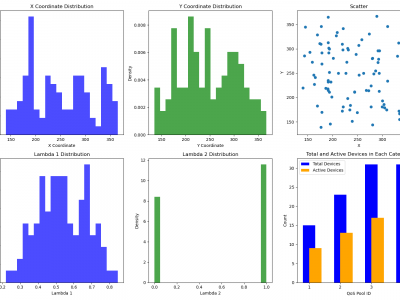
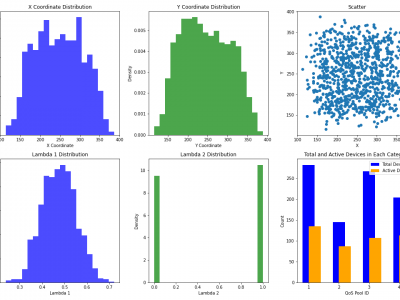
259 ViewsIn our research, we generate datasets utilizing two key statistical models: the Poisson Process Distribution and the Beta Distribution. These models are employed to simulate and analyze various aspects of Quality of Service (QoS) in Internet of Things (IoT) environments, with a particular emphasis on wireless communications. By leveraging these distributions, our study aims to optimize resource allocation, improve reliability, and ensure that QoS requirements are met in complex and dynamic wireless communication scenarios within IoT ecosystems.
- Categories:
 268 Views
268 ViewsTo assist individuals in sports activities is one of the emerging areas of wearable applications. Among various kinds of sports, detecting tennis strokes faces unique challenges. we propose an approach to detect three tennis strokes (backhand, forehand, serve) by utilizing a smartwatch. In our method, the smartwatch is part of a wireless network in which inertial data file is transferred to a laptop where data prepossessing and classification is performed. The data file contains acceleration and angular velocity data of the 3D accelerometer and gyroscope.
- Categories:
 480 Views
480 ViewsIntrusion detection in Unmanned Aerial Vehicle (UAV) networks is crucial for maintaining the security and integrity of autonomous operations. However, the effectiveness of intrusion detection systems (IDS) is often compromised by the scarcity and imbalance of available datasets, which limits the ability to train accurate and reliable machine learning models. To address these challenges, we present the "CTGAN-Enhanced Dataset for UAV Network Intrusion Detection", a meticulously curated and augmented dataset designed to improve the performance of IDS in UAV environments.
- Categories:
 1216 Views
1216 ViewsThis dataset comprises a range of features, including time slots, device IDs, geographic coordinates (x, y), energy consumption, uplink history, emergency status, QoS pool identifiers, data flags, resource IDs, and data sizes. The device locations are modeled using a Poisson distribution with a spread of \(100\) meters within a \(500 \times 500\) meter area. The uplink history, QoS pool assignments, and data flags are derived from the probabilities of data availability and priority values.
- Categories:
 357 Views
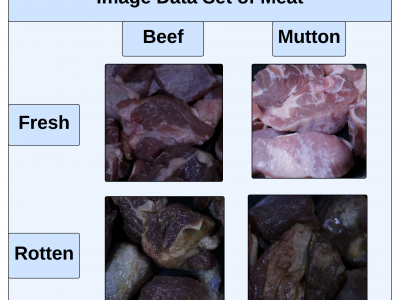
357 ViewsThis paper presents an innovative Internet of Things (IoT) system that integrates gas sensors and a custom Convolutional Neural Network (CNN) to classify the freshness and species of beef and mutton in real time. The CNN, trained on 9,928 images, achieved 99% accuracy, outperforming models like ResNet-50, SVM, and KNN. The system uses three gas sensors (MQ135, MQ4, MQ136) to detect gases such as ammonia, methane, and hydrogen sulfide, which indicate meat spoilage.
- Categories:
 503 Views
503 Views