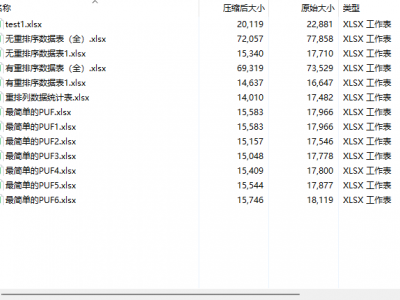
PUF
The dataset is based on PYTHON and machine modeling of 5000 challenge response pairs for both regular CRO PUFs and HMCRO PUFs.This includes the design of reordering schemes
The dataset is based on PYTHON and machine modeling of 5000 challenge response pairs for both regular CRO PUFs and HMCRO PUFs.This includes the design of reordering schemes
The dataset is based on PYTHON and machine modeling of 5000 challenge response pairs for both regular CRO PUFs and HMCRO PUFs.This includes the design of reordering schemes
- Categories:
 149 Views
149 ViewsThe security of systems with limited resources is essential for deployment and cannot be compromised by other performance metrics such as throughput. Physically Unclonable Functions (PUFs) present a promising, cost-effective solution for various security applications, including IC counterfeiting and lightweight authentication. PUFs, as security blocks, exploit physical variations to extract intrinsic responses based on applied challenges, with Challenge-Response Pairs (CRPs) uniquely defining each device.
- Categories:
 404 Views
404 ViewsSecuring systems with limited resources is crucial for deployment and should not be compromised for other performance metrics like area and throughput. Physically Unclonable Functions (PUFs) emerge as a cost-effective solution for various security applications, such as preventing IC counterfeiting and enabling lightweight authentication. In the realm of memory-based PUFs, the physical variations of available memory systems, such as DRAM or SRAM, are exploited to derive an intrinsic response based on the accessed data row.
- Categories:
 346 Views
346 ViewsPhysically unclonable functions (PUFs) are foundational components that offer a cost-efficient and promising solution for diverse security applications, including countering integrated circuit (IC) counterfeiting, generating secret keys, and enabling lightweight authentication. PUFs exploit semiconductor variations in ICs to derive inherent responses from imposed challenges, creating unique challenge-response pairs (CRPs) for individual devices. Analyzing PUF security is pivotal for identifying device vulnerabilities and ensuring response credibility.
- Categories:
 583 Views
583 Views