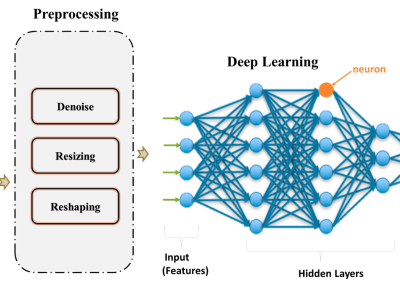
The dataset is a structured image dataset designed to facilitate spatial localization, pattern recognition, and character classification research. It contains high-resolution images of 53 distinct alphabet characters, each systematically placed within a standardized 5×5 grid layout.
- Categories: