malware
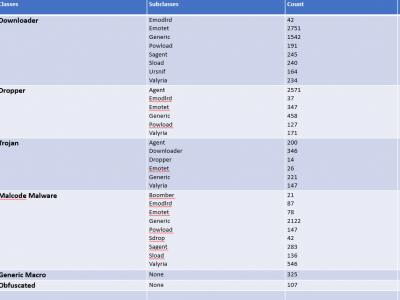
Microsoft contains a productive tool known as MS Office but the inclusion of VBA Macros inside the MS Office for automation purposes makes it a way for attackers to perform malicious activities. To get an up-to-date dataset, the research regarding VBA macros is still working to find efficient ways to detect it. To perform analysis, the dataset is required which is publically harder to find. To overcome this issue, a dataset is created from VirusTotal, VirusShare, Zenodo, Malware Bazaar, Github and InQuest Labs.
- Categories:
 1196 Views
1196 Views
Image representation of Malware-benign dataset. The Dataset were compiled from various sources malware repositories: The Malware-Repo, TheZoo,Malware Bazar, Malware Database, TekDefense. Meanwhile benign samples were sourced from system application of Microsoft 10 and 11, as well as open source software repository such as Sourceforge, PortableFreeware, CNET, FileForum. The samples were validated by scanning them using Virustotal Malware scanning services. The Samples were pre-processed by transforming the malware binary into grayscale images following rules from Nataraj (2011).
- Categories:
 524 Views
524 Views
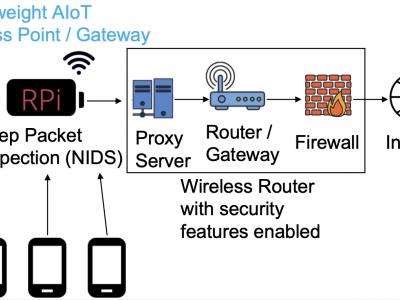
This dataset accurately models the internal behavior of an IoT spectrum sensor (belonging to the ElectroSense platform and consisting of a Raspberry Pi 3 with a software-defined radio kit) when it is functioning normally and under attack. To accomplish it, the system calls of the IoT sensor are monitored under normal behavior, gathered, cleaned, and stored in a centralized directory. Then, the device is infected with current malware affecting IoT devices, such as the Bashlite botnet, Thetick backdoor, Bdvl rootkit, and a Ransomware proof of concept.
- Categories:
 1389 Views
1389 ViewsThis dataset is part of my Master's research on malware detection and classification using the XGBoost library on Nvidia GPU. The dataset is a collection of 1.55 million of 1000 API import features extract from jsonl format of the EMBER dataset 2017 v2 and 2018. All data is pre-processing, duplicated records are removed. The dataset contains 800,000 malware and 750,000 "goodware" samples.
- Categories:
 16567 Views
16567 Views
This dataset is composed of side channel information (e.g., temperatures, voltages, utilization rates) from computing systems executing benign and malicious code. The intent of the dataset is to allow aritificial intelligence tools to be applied to malware detection using side channel information.
- Categories:
 1019 Views
1019 ViewsThis dataset is part of my PhD research on malware detection and classification using Deep Learning. It contains static analysis data: Top-1000 imported functions extracted from the 'pe_imports' elements of Cuckoo Sandbox reports. PE malware examples were downloaded from virusshare.com. PE goodware examples were downloaded from portableapps.com and from Windows 7 x86 directories.
- Categories:
 7692 Views
7692 ViewsThis dataset is part of my PhD research on malware detection and classification using Deep Learning. It contains static analysis data: Raw PE byte stream rescaled to a 32 x 32 greyscale image using the Nearest Neighbor Interpolation algorithm and then flattened to a 1024 bytes vector. PE malware examples were downloaded from virusshare.com. PE goodware examples were downloaded from portableapps.com and from Windows 7 x86 directories.
- Categories:
 3409 Views
3409 ViewsThis dataset is part of my PhD research on malware detection and classification using Deep Learning. It contains static analysis data (PE Section Headers of the .text, .code and CODE sections) extracted from the 'pe_sections' elements of Cuckoo Sandbox reports. PE malware examples were downloaded from virusshare.com. PE goodware examples were downloaded from portableapps.com and from Windows 7 x86 directories.
- Categories:
 3101 Views
3101 ViewsThis dataset is part of our research on malware detection and classification using Deep Learning. It contains 42,797 malware API call sequences and 1,079 goodware API call sequences. Each API call sequence is composed of the first 100 non-repeated consecutive API calls associated with the parent process, extracted from the 'calls' elements of Cuckoo Sandbox reports.
- Categories:
 8900 Views
8900 Views