ToN_IoT datasets

- Citation Author(s):
-
Nour Moustafa
- Submitted by:
- Nour Moustafa
- Last updated:
- DOI:
- 10.21227/fesz-dm97
- Data Format:
- Research Article Link:
- Links:
 15526 views
15526 views
- Categories:
- Keywords:
Abstract
Collecting and analysing heterogeneous data sources from the Internet of Things (IoT) and Industrial IoT (IIoT) are essential for training and validating the fidelity of cybersecurity applications-based machine learning. However, the analysis of those data sources is still a big challenge for reducing high dimensional space and selecting important features and observations from different data sources. The study proposes a new testbed for an IIoT network that was utilised for creating new datasets called TON_IoT that collected Telemetry data, Operating systems data and Network data. The testbed is deployed using multiple virtual machines including hosts of windows, Linux and Kali Linux operating systems to manage the interconnections between the three layers of IIoT, Cloud and Edge/Fog systems. The initial statistical evaluation of the datasets reveals their capability for evaluating cybersecurity applications such as intrusion detection, threat intelligence, adversarial machine learning and privacy-preserving models.
Instructions:
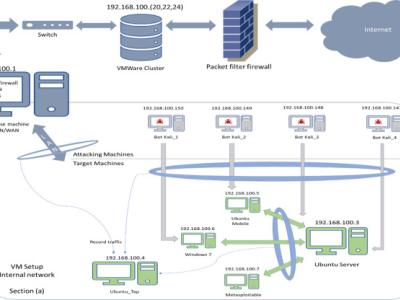
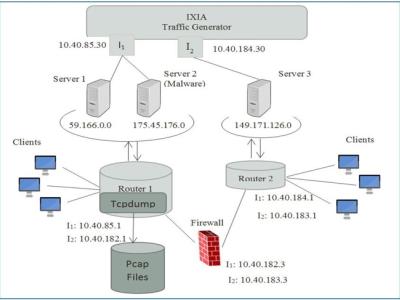
The TON_IoT datasets are new generations of Internet of Things (IoT) and Industrial
IoT (IIoT) datasets for evaluating the fidelity and efficiency of different cybersecurity
applications based on Artificial Intelligence (AI). The datasets have been called
‘ToN_IoT’ as they include heterogeneous data sources collected from Telemetry
datasets of IoT and IIoT sensors, Operating systems datasets of Windows 7 and 10
as well as Ubuntu 14 and 18 TLS and Network traffic datasets. The datasets were
collected from a realistic and large-scale network designed at the IoT Lab of the UNSW
Canberra Cyber, the School of Engineering and Information technology (SEIT), UNSW
Canberra @ the Australian Defence Force Academy (ADFA). The datasets were
gathered in a parallel processing to collect several normal and cyber-attack events
from IoT networks. A new testbed was developed at the IoT lab to connect many virtual
machine, physical systems, hacking platforms, cloud and fog platforms, IoT and IIoT
sensors to mimic the complexity and scalability of industrial IoT and Industry 4.0
networks.
Different hacking techniques, such as DoS, DDoS and ransomware against, were
launched against web applications, IoT gateways and computer systems across the
IIoT network.







In reply to How can i download this data by saad khan
I don't see link for donwloading this dataset , anyhelp please ?