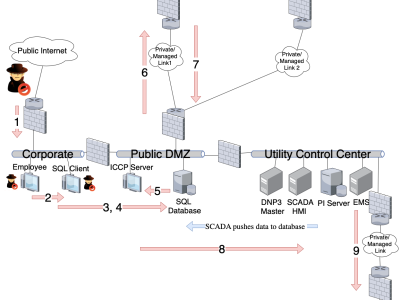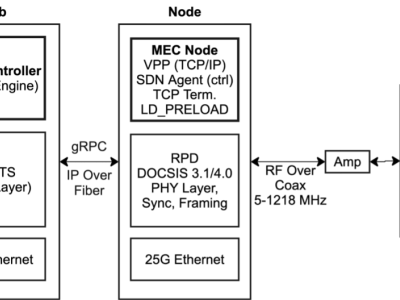
his dataset supports the experimental evaluation of an edge-native architecture for hybrid fiber-coaxial (HFC) networks, where transport-layer (L2–L4) processing is relocated from centralized vCMTS to access-level MEC nodes using the VPP HostStack. While this work focuses on L2–L4 softwarization and transport relocation, application-layer (L5) processing remains out of scope and is identified as a future research direction.
The dataset covers three test scenarios:
- Categories: