Pentesting Methodology
- Citation Author(s):
-
Naman Rastogi
- Submitted by:
- Naman Rastogi
- Last updated:
- DOI:
- 10.21227/fdwv-4d64
- Links:
 452 views
452 views
- Categories:
- Keywords:
Abstract
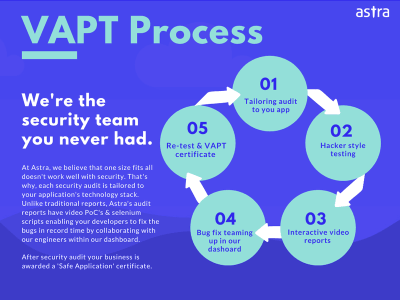
The security testing focuses on evaluating the security of the web, mobile, networks, API, SaaS, blockchain & cloud applications by methodically validating & verifying the effectiveness of security controls. The process involves an active analysis of any application for any available weaknesses, technical flaws, or vulnerabilities.
The security audit scope of work will include:
- Vulnerability Assessment and Penetration Testing (VAPT)
- Static & dynamic code analysis
- Technical assistance in patching found security vulnerabilities
- Collaborative cloud dashboard for vulnerability reporting & management
- Access to our security tools/APIs
- Consultation on the best security practices for your application
Generally, the black box testing include automated pentesting via tools and by an external team (3rd party)
Instructions:
You can simply download the the zip file and can explore it.
Related guide - External Pentesting