Sybil Attack Simulation Dataset
- Citation Author(s):
- Submitted by:
- Muhammad Zunnurain Hussain
- Last updated:
- DOI:
- 10.21227/89w8-bf69
- Data Format:
 492 views
492 views
- Categories:
- Keywords:
Abstract
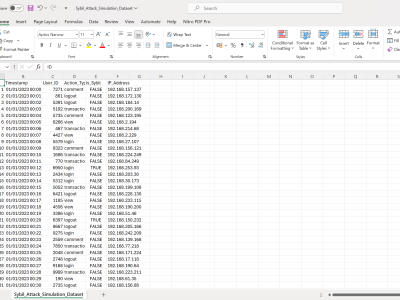
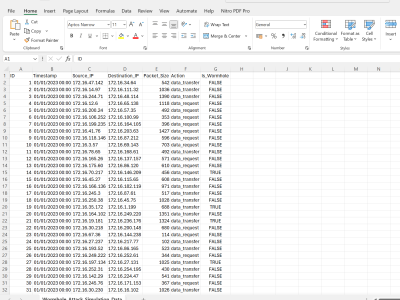
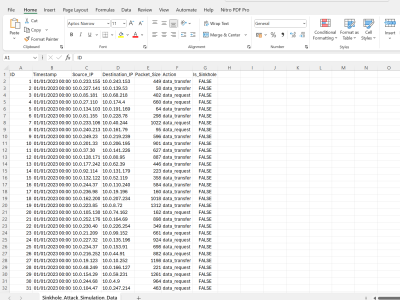
a dataset with 50,000 records simulating a Sybil attack scenario. Here's the plan for each record in the dataset:
- ID: A unique sequential number.
- Timestamp: Randomized date and time.
- User_ID: Randomly assigned, with a pattern to simulate normal and Sybil identities.
- Action_Type: Randomly chosen from a predefined list of actions like login, transaction, comment, etc.
- Is_Sybil: Randomly assigned with a bias towards normal interactions but with a significant portion flagged as Sybil actions to simulate an attack.
- IP_Address: Randomly generated, with Sybil actions often sharing IPs to reflect the nature of the attack.
Instructions:
The dataset is csv file







Researchers doing research on Sybil Attack can get benefit from this dataset.
I would be glad to use this dataset for my research, as I believe it will significantly contribute to my study on sybil attack. The dataset’s relevance and quality will help in conducting a thorough analysis and deriving meaningful insights.
Please let me know if there are any specific terms or conditions for its use. I appreciate your support and look forward to your response.
Best regards,