Datasets
Standard Dataset
Wormhole Attack Simulation Dataset
- Citation Author(s):
- Submitted by:
- Muhammad Zunnur...
- Last updated:
- Tue, 04/16/2024 - 01:52
- DOI:
- 10.21227/da7k-dr50
- License:
 395 Views
395 Views- Categories:
- Keywords:
0 ratings - Please login to submit your rating.
Abstract
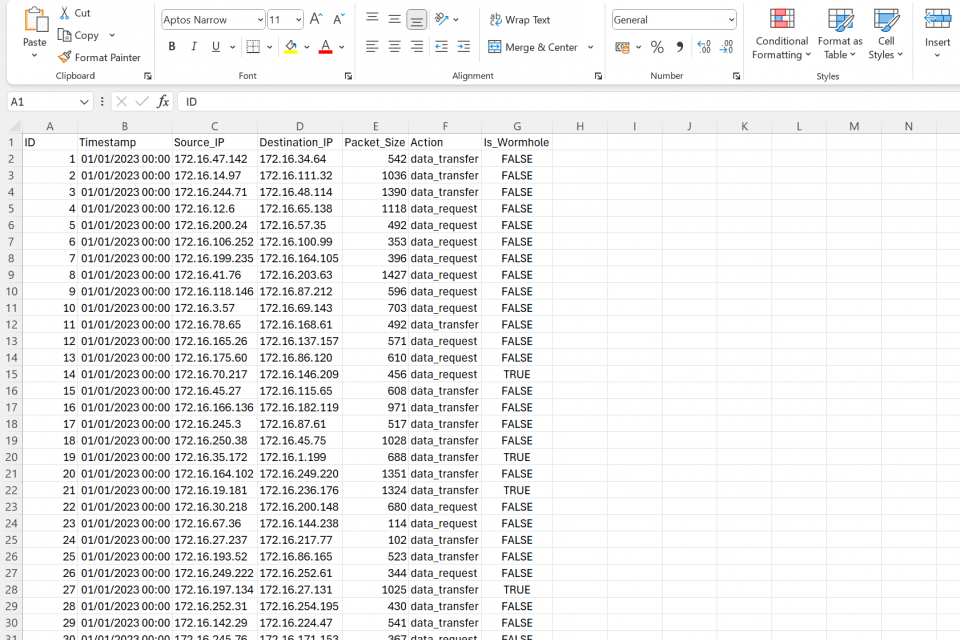
A Wormhole attack in a dataset, where certain nodes (wormhole nodes) create an illusion of having a shorter path in network communications to attract traffic, the dataset will reflect network traffic patterns altered by these deceptive links. Here’s the structure for 95,000 records:
- ID: Unique identifier for each packet or interaction.
- Timestamp: Randomized date and time.
- Source_IP: IP address of the source node.
- Destination_IP: IP address of the destination node.
- Packet_Size: Size of the packet sent from source to destination.
- Action: Type of action (e.g., data_request, data_transfer).
- Is_Wormhole: Indicates if the interaction involved a wormhole node (True or False).
Instructions:
The dataset is for the researchers who are doing research in the security domain
More from this Author








Comments
none
hi