Website Fingerprinting

Our DeepCoAST dataset specifically explores the vulnerabilities of various traffic-splitting Website Fingerprinting (WF) Defenses, such as TrafficSliver, HyWF, and CoMPS. Our dataset comprises defended traces generated from the BigEnough dataset, which includes Tor cell trace instances of 95 websites, each represented by 200 instances collected under the standard browser security level. We simulated the traffic-splitting defenses assuming there are two split traces from the vanilla trace.
- Categories:
 115 Views
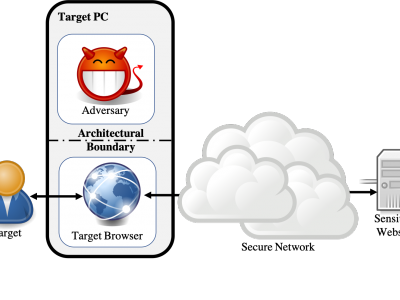
115 ViewsWebsite fingerprinting attacks, which use statistical analysis on network traffic to compromise user privacy, have been shown to be effective even if the traffic is sent over anonymity-preserving networks such as Tor. The classical attack model used to evaluate website fingerprinting attacks assumes an on-path adversary, who can observe all traffic traveling between the user's computer and the secure network.
- Categories:
 1045 Views
1045 Views