Dataset for IAT collection from Real-World IoT Devices
- Citation Author(s):
- Submitted by:
- Lin ZhiJun
- Last updated:
- DOI:
- 10.21227/sjby-3w39
 2086 views
2086 views
- Categories:
Abstract
With the increasing popularity of the Internet of Things (IoT), security issues in the IoT
network have become the focus of research. Since the number of IoT devices connected to the network
has increased, the conventional network framework faces several problems in terms of network latency
and resource overload. Fog computing is intended to construct a new network framework. However, fog
computing has also caused new security challenges, such as authentication, authorization, and secure
communication. In this paper, we proposed a novel device authentication mechanism based on interarrival
time (IAT). We utilized IAT to generate device fingerprints and combined these fingerprints with
the digital certificate to verify IoT devices. Moreover, we utilized IAT fingerprinting to propose a simple,
secure communication and key management framework. To evaluate the proposed framework, we first
used real-world devices to analyze IAT in device fingerprinting. Second, we simulated our framework on
Contiki OS. The results show the effectiveness of IAT device fingerprinting, with an accuracy of ninetynine
percent. We utilized the IAT device fingerprinting mechanism in authentication and the overall
framework of secure communication. The results shows that the proposed method not only reduces the
power consumption for authentication but also impacts the overall communication time.
Instructions:
None





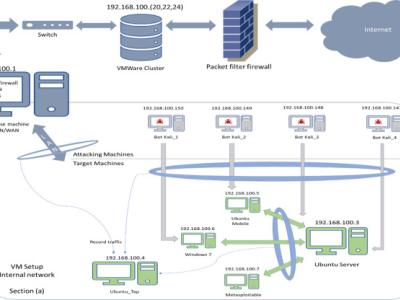
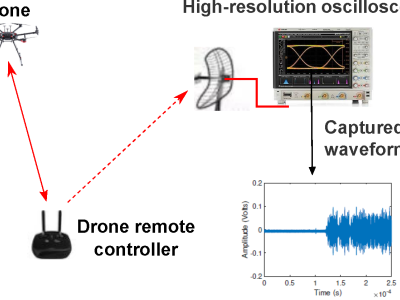

thank you