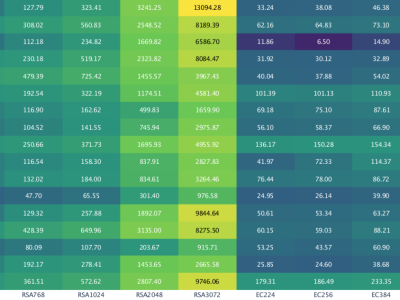
Wearable and low power devices are vulnerable to side-channel attacks, which can retrieve private data (like sensitive data or the private key of a cryptographic algorithm) based on externally measured magnitudes, like power consumption. These attacks have a high dependence on the data being encrypted -- the more variable it is, the more information an attacker will have for performing it. This database contains ECG data measured with a wearable sensorized garment during different levels of activity.
- Categories: