
Cacheaccel Simulator trace files and project files are uploaded.
- Categories:

Cacheaccel Simulator trace files and project files are uploaded.
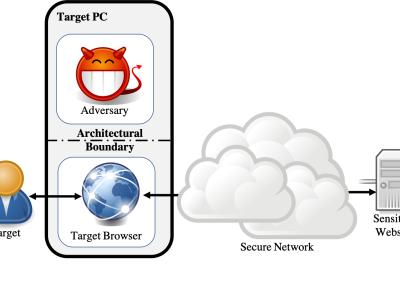
Website fingerprinting attacks, which use statistical analysis on network traffic to compromise user privacy, have been shown to be effective even if the traffic is sent over anonymity-preserving networks such as Tor. The classical attack model used to evaluate website fingerprinting attacks assumes an on-path adversary, who can observe all traffic traveling between the user's computer and the secure network.