MM-TBM evaluation datasets
- Citation Author(s):
-
Natalie Clewley
- Submitted by:
- Georgios Ioannou
- Last updated:
- DOI:
- 10.21227/8dt8-gx46
- Data Format:
- Research Article Link:
 479 views
479 views
- Categories:
- Keywords:
Abstract
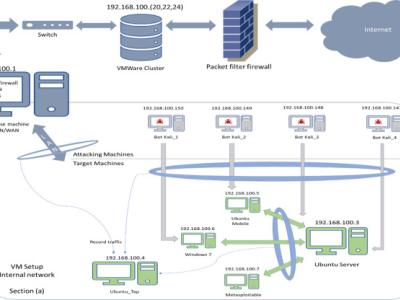
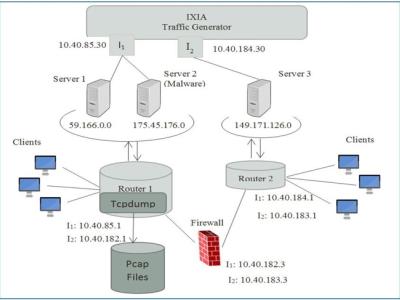
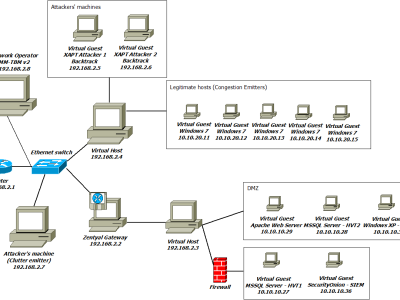
These datasets were generated in a computer network environment where eXfiltration Advanced Persistent Threats were launched against a number of high-value targets.
It is the alert log of the Security Onion SIEM which aggregates alerts from network and host-based intrusion detection systems that are securing the network environment.
Background traffic and attack clutter (noise) are also injected in the network alongside the cyber attacks. In order to confuse the algorithm, clutter attacks generate similar evidence to that of the cyber attack that relatess to the ground truth.
Instructions:
To use the dataset, first convert the columns 4 and 5 from decimal to IP format.
The dataset is unlabelled. To test the dataset with MM-TBM you have to assign a set of belief assignments to each packet with relevance to a specific Alert frame of discernment.