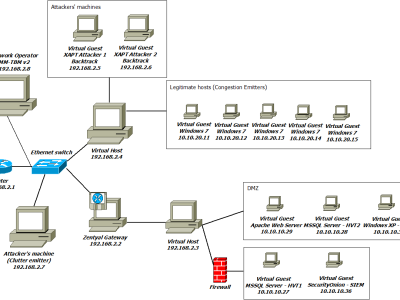
This work intend to identify characteristics in network traffic that are able to distinguish the normal network behavior from denial of service attacks. One way to classify anomalous traffic is the data analysis of the packets header. This dataset contains labeled examples of normal traffic (23.088 instances), TCP Flood attacks (14.988 instances), UDP Flood (6.894 instances), HTTP Flood (347 instances) and HTTP Slow (183 instances) distributed in 73 numeric variables.
- Categories: