Datasets
Standard Dataset
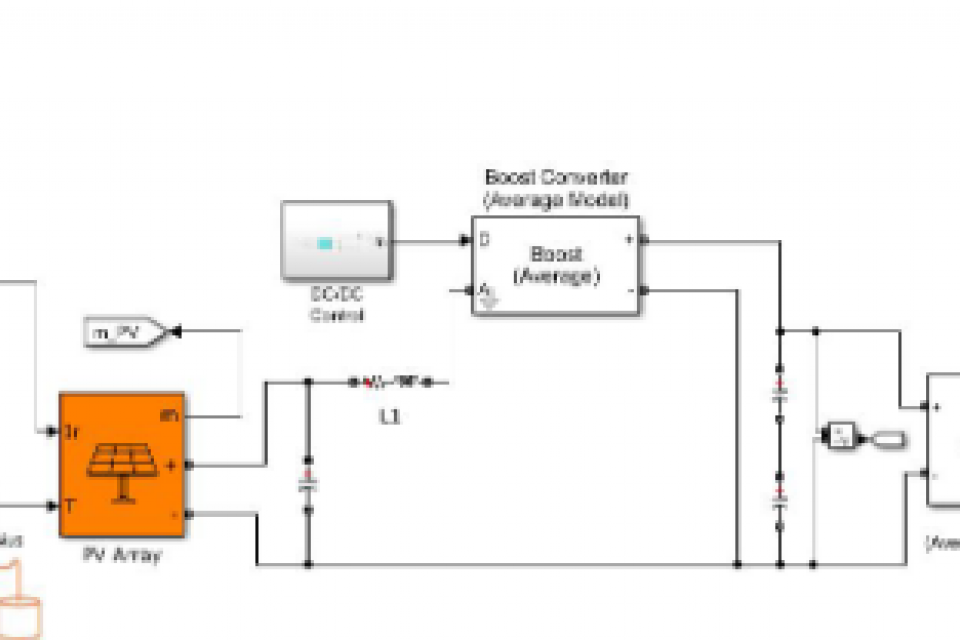
Photo-Set: A Dataset for Physics-Based Cybersecurity Monitoring in a Photovoltaic System
- Citation Author(s):
- Submitted by:
- Giovanni Battis...
- Last updated:
- Tue, 09/03/2024 - 17:30
- DOI:
- 10.21227/e4zm-h695
- Data Format:
- Research Article Link:
- License:
 362 Views
362 Views- Categories:
- Keywords:
0 ratings - Please login to submit your rating.
Abstract
Smart grids today are characterized by the integration of distributed energy resources, including renewable energy sources, traditional power sources, and storage systems. These components typically employ various control technologies that interface with generators through smart inverters, making them susceptible to numerous cyber threats. To address this vulnerability, there is a crucial need for datasets that document attacks on these systems, enabling risk evaluation and the development of effective monitoring algorithms. This dataset
responds to this need by introducing Photo-Set, an open-source dataset designed for the cybersecurity analysis of photovoltaic systems.
Instructions:
All the instructions are in the README files
Funding Agency:
SERICS under the MUR National Recovery and Resilience Plan funded by the European Union - NextGenerationEU
Grant Number:
PE00000014






Comments
Dear Giovanni B.,
I hope this message finds you well. I am reaching out to introduce myself and to inquire about data access for advancing my current research interests.
I recently completed my postdoctoral research at Geneva University, where I developed a comprehensive framework of security and privacy-by-design guidelines for IoT, spanning from the physical layer to cloud-stored data and mapping relationships among guidelines, attacks, and mitigation strategies. This work resulted in four IEEE Open Access publications.
Building on this foundation, I aim to analyze datasets that support cybersecurity and data science, focusing on assessing the effectiveness of security guidelines. Specifically, I intend to:
Given the goals of your project, Photo-Set, I believe this dataset could be pivotal in my research. Could you kindly share access? I look forward to the potential insights it could enable.
Thank you for considering my request.
Best regards,
Akram