AITSteg: An Innovative Text Steganography Technique for Hidden Transmission of Text Message via Social Media
- Citation Author(s):
-
Milad Taleby Ahvanooey
- Submitted by:
- Milad Taleby Ahvanooey
- Last updated:
- DOI:
- 10.21227/sjsz-1r61
- Data Format:
- Research Article Link:
 812 views
812 views
- Categories:
- Keywords:
Abstract
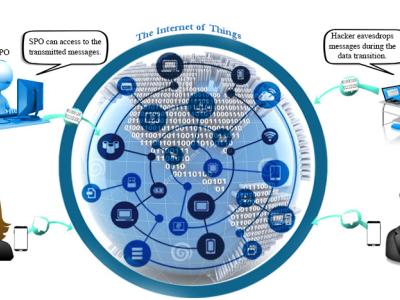
With the popularity of smartphones and widespread use of high-speed Internet, social media has become a vital part of people’s daily life. Currently, text messages are used in many applications, such as mobile chatting, mobile banking, and mobile commerce. However, when we send a text message via short message service (SMS) or social media, the information contained in the text message transmits as a plain text, which exposes it to attacks. In some cases, this information may be confidential, such as banking credentials, secret missions, and confidential appointments; moreover, it is a major drawback to send such information via SMS or social media, as neither provides security before transmission. In this study, we propose a novel text steganography technique called AITSteg, which provides end-to-end security during the transmission of text messages via SMS or social media between end users. The AITSteg technique is evaluated by considering a trusted scenario. We then evaluate the efficiency of the proposed technique in terms of embedding capacity, invisibility, robustness, and security. The experiments confirm that the AITSteg is able to prevent various attacks, including man-in-the-middle attacks, message disclosure, and manipulation by readers. Moreover, we compare the experimental results with the existing techniques to show the superiority of the proposed technique. To the best of our knowledge, this is the first text steganography technique that provides end-to-end secure transmission of the text message using symmetric keys via social media.
Instructions:
This is a readme for running the AITSteg Technique.