
This dataset is generated by GNU Radio.
- Categories:

This dataset is generated by GNU Radio.

By introducing high randomness with reduced computational cost, physical layer (PHY) key generation is one of the candidate tools which can be used for the security of the Internet of Things (IoT) applications. Non-identical secret keys are one of the main problems of the physical layer (PHY) key generation schemes. In order to address this problem, key verification schemes which are based on information reconciliation are used. In the current key verification techniques, the legitimate nodes reveal some information related to their secret keys in order to eliminate non-identical bits.

GENERATION OF MODE SELECTION PROBABILITY - SINGLE RATE CASE, IMPORTANCE OF DIRECT PATH, COMPARISON WITH CONVENTIONAL INCREMENTAL SCHEME
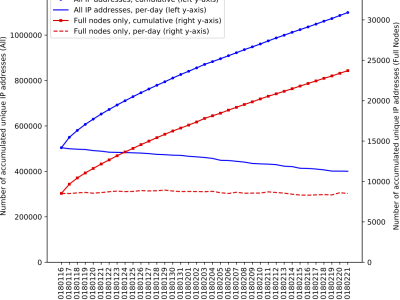
Bitcoin is a decentralized digital currency that has gained significant attention and growth in recent years. Unlike traditional currencies, Bitcoin does not rely on a centralized authority to control the supply, distribution, and verification of the validity of transactions. Instead, Bitcoin relies on a peer-to- peer network of volunteers to distribute pending transactions and confirmed blocks, verify transactions, and to collectively implement a replicated ledger that everyone agrees on. This peer-to-peer (P2P) network is at the heart of Bitcoin and many other blockchain technologies.

The Monte Carlo method (MCM) is known as the gold standard technique for uncertainty quantification (UQ). However, it requires a considerable number of simulations leading to excessive computational resources.
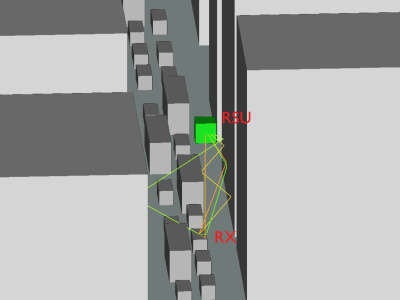
Data and codes for journal paper "MmWave Vehicular Beam Training with Situational Awareness Using Machine Learning" submitted to IEEE Access.
The code assumes Python 3.

1. Figure S1 shows the plasma frequency profile of the two-layer analytical model of the ionosphere, see Eq. (9) of the main text.
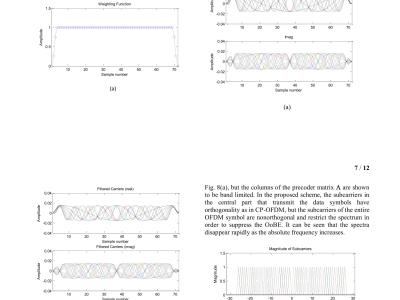
A spectrally encapsulated orthogonal frequency division multiplexing (SE-OFDM) precoding scheme for short packet transmission that is able to suppress the out-of-band emission (OoBE) while maintaining the advantage of thecyclic prefix (CP)-OFDM is proposed. The SE-OFDM symbol consists of a prefix, an information (I)-symboland a suffix that are generated by head, center and tail matrices, respectively.

HTTP and DNS sample traffic traces for experimenting of protocol reverse engineering methods.

The dataset is used in the paper entitled "A distributed Fog node assessment model by using Fuzzy rules learned by XGBoost" as fuzzy rules extracted by XGboost