Coperfed

- Citation Author(s):
-
Yao Shan
- Submitted by:
- Yao Shan
- Last updated:
- DOI:
- 10.21227/r97x-0222
 50 views
50 views
- Categories:
- Keywords:
Abstract
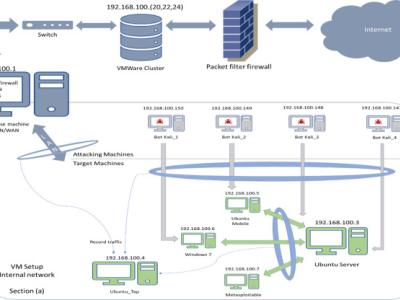
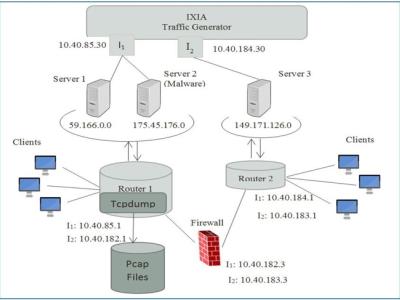
The coperfed dataset, which contains four datasets:ICS traffic data, low-interaction ICS honeypot data, high-interaction ICS honeypot data, attack tools data. ICS traffic data is collected in a simulated power system with two MTUs and six RTUs, and the traffic includes six types of attack traffic as well as regular system polling and manual operation traffic. The low-interaction ICS honeypot data are traffic from 10 different attacking organizations collected by a Modbus honeypot developed by from July 2017 to February 2023. Traffic from the same organization is regarded as belonging to the same category of attacks. High-interaction ICS Honeypot Data from , which creates a high-interaction Modbus honeypot that highly simulates a water treatment PLC device from the perspective of a physical process. The dataset contains four types of attack traffic data collected by this honeypot. The attack tools data is collected from ten Modbus industrial control devices using five publicly accessible attack tools implemented on GitHub, with 1000 scans per device.
Instructions:
coperfed 数据集,包含四个数据集:ICS 流量数据、低交互 ICS 蜜罐数据、高交互 ICS 蜜罐数据、攻击工具数据。ICS 流量数据在具有 2 个 MTU 和 6 个 RTU 的模拟电力系统中收集,流量包括 6 种类型的攻击流量以及常规系统轮询和手动操作流量。低交互 ICS 蜜罐数据是 2017 年 7 月至 2023 年 2 月期间开发的 Modbus 蜜罐收集的来自 10 个不同攻击组织的流量。来自同一组织的流量被视为属于同一类别的攻击。High-interaction ICS Honeypot Data from ,它创建了一个高交互性 Modbus 蜜罐,从物理过程的角度高度模拟了水处理 PLC 设备。该数据集包含该蜜罐收集的 4 种类型的攻击流量数据。攻击工具数据是使用 GitHub 上实施的 5 种可公开访问的攻击工具从 10 台 Modbus 工业控制设备中收集的,每台设备进行 1000 次扫描。