Open Access Entries from this Author

Cloud forensics is different than digital forensics because of the architectural implementation of the cloud. In an Infrastructure as a Service (IaaS) cloud model. Virtual Machines (VM) deployed over the cloud can be used by adversaries to carry out a cyber-attack using the cloud as an environment.
- Categories:
Category
Dataset Entries from this Author
The dataset contains memory dump data which is generated continuously. For the experiment we carried out, we implemented the volatile data dump module which generated around 360 VM memory dump images of average size 800Mb each (Total 288GB). These data files are compressed using gzip utility. Further zipped to 79.5GB one single file of memory evidence.
Out of these preserved and stored memory dump dataset, 79 files of size 17.3GB were generated during the attack. This means the data 21.76% of data (in size) is potential evidence.
- Categories:
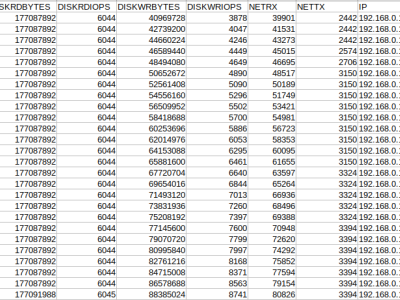
Intrusion Detection System can be build for private cloud using OpenNebula. OpenNebula is a cloud computing platform for managing heterogenous distributed data center infrastructure. The database is generated using a private cloud setup using KVM and OpenNebula. OpenNebula provides API to monitor Virtual Machines (VMs) running on the infrastructure. Total 6 VMs were deployed on the infrastructure. The monitoring data was collected over 63 Hours. Attacks were simulated on few of the VMs for variable time duration.
- Categories:
