Tackling the Optimal Phasor Measurement Unit Placement and Attack Detection Problems in Smart Grids by Incorporating Machine Learning
- Submission Dates:
-
to
- Citation Author(s):
-
Mohamed S. Abdalzaher
- Submitted by:
- Mohamed Salah Abdalzaher
- Last updated:
- DOI:
- 10.21227/g7vk-1p32
- Categories:
- Keywords:
Abstract
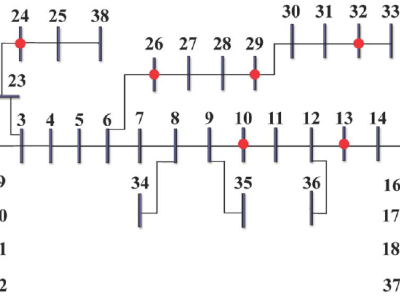
<p>Smart grid cybersecurity is a critical research challenge due to society's dependence on reliable electricity. Existing research primarily addresses cybersecurity by focusing on the optimal placement of phasor measurement units (PMUs) to ensure topological observability and minimize system costs, followed by developing AI-based attack detection algorithms. However, these studies fail to simultaneously consider system cost, loss in system observability, and false data injection attack (FDIA) detection performance. Thus, this paper proposes a novel approach by formulating this issue as a tri-objective functions optimization problem. The proposed approach optimizes PMU allocation to maximize topological observability and minimize system cost while improving the FDIA detection performance using machine learning. Specifically, the k-Nearest Neighbors (KNN) model's Brier loss is used as an objective function within the Non-Dominated Sorting Genetic Algorithm II (NSGA-II) optimization framework to represent the FDIA detection performance. To demonstrate the proposed approach's efficacy, it is tested on the IEEE 38-bus distribution system. To verify the strength of the developed KNN classifier, we examined it using seven different metrics: accuracy, brier loss, F1-score, elapsed time, learning curve, receiver operating characteristic curve (ROC) curve, and confusion matrix. The simulation results show that the KNN model achieved superior attack classification performance with a top accuracy of 99.99\% and {a minimal Brier loss} of $9.9478 \times 10^{-4}$ on the $\pm0.2\%$ PMU observation tolerance dataset. These results highlight the success of our framework in concurrently optimizing attack detection performance, topological observability, and system cost.</p>
Instructions:
Please follow the code's sequence.


