Security

This dataset comprises over 38,000 seed inputs generated from a range of Large Language Models (LLMs), including ChatGPT-3.5, ChatGPT-4, Claude-Opus, Claude-Instant, and Gemini Pro 1.0, specifically designed for the application in fuzzing Python functions. These seeds were produced as part of a study evaluating the utility of LLMs in automating the creation of effective fuzzing inputs, a method crucial for uncovering software defects in the Python programming environment where traditional methods show limitations.
- Categories:
 175 Views
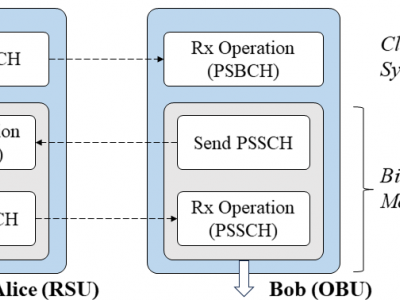
175 ViewsTo test the reciprocity of V2X channel, bidirectional channel state information (CSI) measurement is conducted between Alice (RSU) and Bob (OBU) through PSSCH signal. We utilized two USRP X310 SDR platforms equipped with the CBX daughter board as Alice and Bob. Despite the designed fast USRP transceiver switching, there is a signal transmission delay of approximately 0.3 ms, resulting in a gap of about 4 to 5 symbols in the PSSCH subframe actually received by Alice and Bob.
- Categories:
 402 Views
402 Views
This data reflects the prevalence and adoption of smart devices. The experimental setup to generate the IDSIoT2024 dataset is based on an IoT network configuration consisting of seven smart devices, each contributing to a diverse representation of IoT devices. These include a smartwatch, smartphone, surveillance camera, smart vacuum and mop robot, laptop, smart TV, and smart light. Among these, the laptop serves a dual purpose within the network.
- Categories:
 1256 Views
1256 Views
The data was built in order to evaluate behavior of the Word Error Rate (WER) of the adversaries' and victims' Error Correcting Codes for different symbol error probability (channel errors) is affected by different code parameters for the adversaries' Error Correcting Code.
For the non-binary communication channel with a GRS based covert channel WER of the victims' Error Correcting Code are shifted to the right as the minimal distance of the adversaries' Error Correcting Codes decrease.
- Categories:
 122 Views
122 ViewsThe security of systems with limited resources is essential for deployment and cannot be compromised by other performance metrics such as throughput. Physically Unclonable Functions (PUFs) present a promising, cost-effective solution for various security applications, including IC counterfeiting and lightweight authentication. PUFs, as security blocks, exploit physical variations to extract intrinsic responses based on applied challenges, with Challenge-Response Pairs (CRPs) uniquely defining each device.
- Categories:
 299 Views
299 Views
In deep learning, images are utilized due to their rich information content, spatial hierarchies, and translation invariance, rendering them ideal for tasks such as object recognition and classification. The classification of malware using images is an important field for deep learning, especially in cybersecurity. Within this context, the Classified Advanced Persistent Threat Dataset is a thorough collection that has been carefully selected to further this field's study and innovation.
- Categories:
 1532 Views
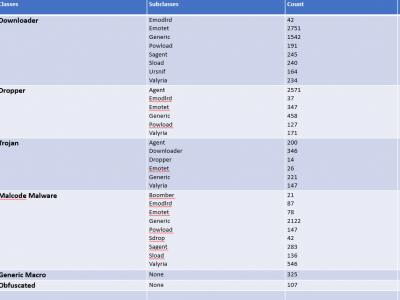
1532 ViewsMicrosoft contains a productive tool known as MS Office but the inclusion of VBA Macros inside the MS Office for automation purposes makes it a way for attackers to perform malicious activities. To get an up-to-date dataset, the research regarding VBA macros is still working to find efficient ways to detect it. To perform analysis, the dataset is required which is publically harder to find. To overcome this issue, a dataset is created from VirusTotal, VirusShare, Zenodo, Malware Bazaar, Github and InQuest Labs.
- Categories:
 1042 Views
1042 Views
The WPT dataset was specially created for "Web Page Tampering Detection Based on Dynamic Temporal Graph Pre-training" and encompasses over 200,000 regular web pages from 75 websites across the finance, healthcare, and education sectors, in addition to 1,541 tampered examples sourced from zone-h.org. This dataset organizes web pages as nodes and their links as edges within a discrete dynamic graph structure, capturing snapshots at various moments in time. Each node integrates structural, textual, and statistical features into a robust 148-dimensional feature vector for every page.
- Categories:
 61 Views
61 Views
The sudden shift from physical office location to a fully remote or hybrid work model accelerated by the COVID-19 pandemic is a phenomenon that changed how organizations traditionally operated and thereby introduced new vulnerabilities and consequently changed the cyber threat landscape. This has led organizations around the globe to seek new approaches to protect their enterprise network. One such approach is the adoption of the Zero Trust security approach due to its many advantages over the traditional/perimeter security approach.
- Categories:
 470 Views
470 ViewsA Wormhole attack in a dataset, where certain nodes (wormhole nodes) create an illusion of having a shorter path in network communications to attract traffic, the dataset will reflect network traffic patterns altered by these deceptive links. Here’s the structure for 95,000 records:
- Categories:
 305 Views
305 Views