Communications
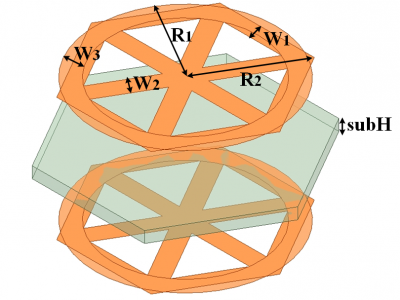
The design of this ASS structure is based on a dual-layer frequency-selective surface (FSS), where the unit cell consists of a single substrate and two metal layers. This structure achieves resonant transmission at specific oblique angles while blocking electromagnetic (EM) waves at other angles. In addition, the equivalent circuit model (ECM) is utilized to analyze the proposed structure, revealing the influence of oblique incidenc on circuit parameters.
- Categories:
 176 Views
176 ViewsThis dataset consists of network packet traces collected in 2023 on the 5G infrastructure deployed at Chalmers University of Technology.
The dataset includes 1,912 pcap files, distributed across 8 folders. Each pcap file captures 1 minute of encrypted network traffic generated by one of the following 8 popular mobile applications:
- Categories:
 437 Views
437 ViewsThe Multi-Server Multi-User computation offloading dataset is a dataset based on the scenario of multi-server multi-user binary computing offloading. It is characterized by the connection status between users and edge servers, user task information, and server computational resource information. The solution aims to minimize the total cost of power consumption and latency of all tasks. The labels are the offloading decisions of user tasks and the computational resource allocation of edge servers. The features and labels of this dataset are graph-structured.
- Categories:
 152 Views
152 ViewsThe TiHAN-V2X Dataset was collected in Hyderabad, India, across various Vehicle-to-Everything (V2X) communication types, including Vehicle-to-Vehicle (V2V), Vehicle-to-Infrastructure (V2I), Infrastructure-to-Vehicle (I2V), and Vehicle-to-Cloud (V2C). The dataset offers comprehensive data for evaluating communication performance under different environmental and road conditions, including urban, rural, and highway scenarios.
- Categories:
 559 Views
559 ViewsThe Unified Multimodal Network Intrusion Detection System (UM-NIDS) dataset is a comprehensive, standardized dataset that integrates network flow data, packet payload information, and contextual features, making it highly suitable for machine learning-based intrusion detection models. This dataset addresses key limitations in existing NIDS datasets, such as inconsistent feature sets and the lack of payload or time-window-based contextual features.
- Categories:
 758 Views
758 Views
The dataset consists of uplink channel gains, downlink channel gains and uplink to downlink channel gains along with corresponding power allocations for uplink users and downlink users across all subcarriers. Additionally, it consists of NOMA decoding order for successful implementation of SIC at NOMA receiver. The number of UL users and DL users are considered as N=M=6, and subcarriers are S=9. Each column in the dataset is a sample for fading channel realization and it should be converted back to the matrix to compute sumrate.
- Categories:
 120 Views
120 Views
Today, the anywhere, anyhow and anytime application scenarios of 5G system force designer to challenge on electromagnetic interference (EMI) requirements. Despite the technological progress, relevant test techniques are necessary to minimize the future communication system EMI risk. In this paper, the EMI characterization from nonlinearity (NLT) of 5G system Gallium Nitride (GaN) power amplifier (PA) is studied. Firstly, the PA NLT is evaluated by 1-dB/3-dB/6-dB compression point and 3rd-order intermodulation distortion (IMD3).
- Categories:
 125 Views
125 Views
The softwarization and virtualization of the fifth-generation (5G) cellular networks bring about increased flexibility and faster deployment of new services. However, these advancements also introduce new vulnerabilities and unprecedented attack surfaces. The cloud-native nature of 5G networks mandates detecting and protecting against threats and intrusions in the cloud systems.
- Categories:
 200 Views
200 Views
Common Randomness (CR) can be considered as a resource in our future communication systems that will assist in various operations, such as cryptographic encryption in wireless communication, improving identification capacity for identification codes. In wireless communication, CR can be conveniently generated by reading the reciprocal channel properties between two wireless terminals, and by sending pilot signals to each other using the time division duplexing (TDD)-based half-duplexing method. In the channel probing stage, reciprocal channel characteristics are measured.
- Categories:
 80 Views
80 ViewsTo download the dataset without purchasing an IEEE Dataport subscription, please visit: https://zenodo.org/records/13738598
Please cite the following paper when using this dataset:
- Categories:
 958 Views
958 Views